| In any system, password is stored in a file and contents
are obscured such that only
authentication
can validate the user login/password.
Salt is random text concatenated to a user created plain text
password to make the hash
value unique hash(salt+password). Initially password used to
be stored as plain text in a file and generic access control managed the security
of the password file. Later the plain text password was hashed
hash(password).
Hasing of plain text password is a weak form of security.
|
| |
|
Encrypted password = hash(salt + password)
|
| |
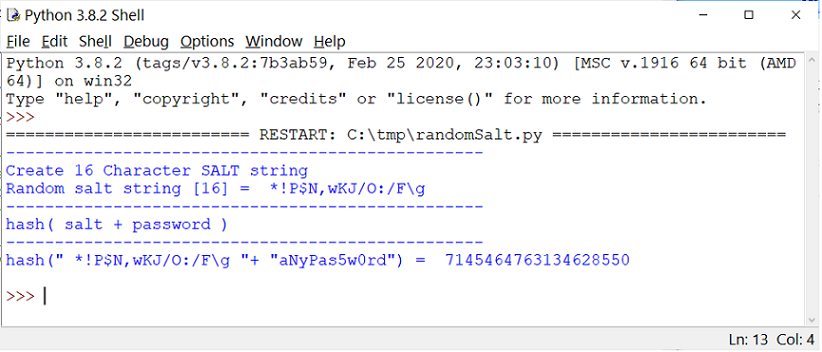
| Python output:
Encrypted password = hash('*!P$N,wKJ/O:/F\g'+'aNyPas5w0rd')
|
| |
|
| |
|
As an example the 16-characters value "*!P$N,wKJ/O:/F\g"
is concatenated to the
plain password text (aNyPas5w0rd) to get an
encrypted hash password. Generally the hash
function is uni-directional, the plain text password value cannot be easily
derived (reverse engineered) by "Unhashing". The password can be further
secured as shown below.
|
| |
|
Encrypted password = hash(salt + hash(password))
|
| |
|
The random salt value is created for each user (username). By hashing (salt and
password) the value will be unique even if by any chance the password is
the same for a few users.
|
| |
|
Most applications have
front end UI
(web, mobile etc.) for data input and backend database to store data. In
these applications, to secure the web or front end application code, a
plain text referred as pepper is encrypted first and
added to the password
string. This adds another security layer to the application. In the
event of a
SQL injection
attack, the web/front end code is not impacted. The pepper is typically
stored in the application server where the front code resides. The database
is hosted on a database server and only the hashed password may be
stored.
|
| |
|
Encrypted password = hash(encrypt(pepper) + salt + password)
|
| |
|
When applications are enhanced, a new value of pepper is generated, encrypted
and stored securely during the build process. This minimizes rainbow
table attack.
NIST recommends use of
PBKDF2 to hash passwords.
|
| |
|
Derivative Key (DK) = PBKDF2(PRF, Password, Salt, n, bLen)
|
| |
|
PRF (pseudo random function) with two input parameters and output of nLen (length)
|
|
n is the required number of iterations
|
|
bLen is the required bit-length of the derived key
|
| |
| |
| Related Reference |
|
Encryption
|
|
Oracle Database Encryption and Decryption
|
